Trusted Moving Solutions
Your reliable partner for seamless relocation.
RFID Revelations: A Tag and a Twist
Uncover the secrets of RFID technology with unique twists that will change how you think about tagging! Discover insights and surprises today!
Understanding RFID Technology: How Tags Work and Their Applications
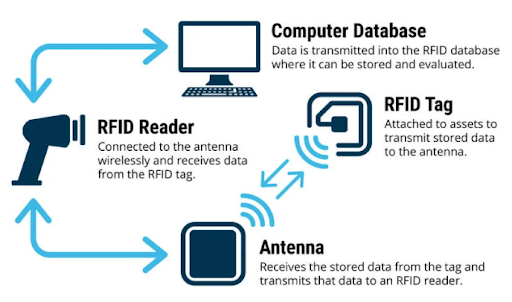
RFID technology, or Radio Frequency Identification, is a wireless system that utilizes electromagnetic fields to automatically identify and track tags attached to objects. These tags contain electronically stored information, which can be read by RFID readers. The basic components of an RFID system include the tag, the reader, and the antenna. Tags come in various forms, such as passive, active, and semi-passive, depending on their power source and communication methods. Passive tags, for instance, rely on the reader's signal for power, whereas active tags have their own battery. Understanding how RFID tags work is crucial for implementing them effectively across different applications.
The applications of RFID technology are vast and continually expanding. Industries like retail, logistics, healthcare, and manufacturing utilize RFID systems to improve inventory management, streamline supply chains, and enhance patient tracking. For example, in retail, RFID tags facilitate real-time inventory visibility, allowing retailers to manage stock more efficiently and reduce losses due to theft or overstock. Additionally, in healthcare, RFID tags are used to monitor the location of equipment and ensure patient safety by preventing mix-ups in medication administration. As organizations recognize the benefits of RFID technology, its adoption is likely to grow exponentially, making it a pivotal part of modern business operations.
Counter-Strike is a popular tactical first-person shooter game that emphasizes teamwork and strategy. Players can choose to play as terrorists or counter-terrorists, aiming to complete objectives such as bomb defusal or hostage rescue. Many gamers enjoy enhancing their gear, and for those looking for stylish utility, check out the Top 10 magsafe wallets that are both functional and fashionable.
The Future of RFID: Innovations and Emerging Trends
The future of RFID technology looks promising as innovations continue to emerge across various sectors. One of the most significant trends is the integration of RFID with Internet of Things (IoT) devices, enhancing real-time data tracking and management. This synergy not only improves supply chain efficiency but also allows for better inventory control and asset management. Companies are increasingly adopting smart RFID solutions that leverage cloud computing and advanced analytics, enabling them to gather actionable insights and optimize operational processes.
Moreover, the ongoing advancements in RFID chip technology are paving the way for more compact, cost-effective, and energy-efficient systems. Future applications may include the use of RFID for contactless payments, personalized shopping experiences, and enhanced patient tracking in healthcare. These innovations are expected to reshape industries and foster greater interconnectedness, making RFID an integral part of the digital landscape. As businesses adapt to these emerging trends, staying ahead of the curve will be crucial for competitiveness and sustainable growth.
Is RFID Secure? Addressing Common Concerns and Misconceptions
The security of RFID technology has become a topic of significant concern among consumers and businesses alike. While RFID systems are generally designed with multiple layers of security, many people still harbor misconceptions about their vulnerability to unauthorized access. One common fear is that RFID tags can be easily scanned by anyone nearby. In actuality, the security protocols in many RFID systems include encryption and authentication measures that help protect sensitive information. Furthermore, advancements in RFID technology are continually enhancing these security features, making them more robust against potential threats.
Another prevalent misconception is that all RFID systems are equally insecure. However, the reality is that the level of security can vary greatly between different RFID applications. For instance, low-frequency (LF) tags often have less robust security compared to ultra-high-frequency (UHF) tags, which may include advanced encryption techniques. It is essential for users to understand that not all RFID implementations are created equal. By opting for systems that comply with industry standards and best practices, organizations can significantly mitigate risks and ensure that their RFID deployments are secure.